June 23, 2009
Reinstall Windows XP Without the CD
Step-by-step
Sometimes manufacturers do not include the Windows XP Operating System CD when you first buy your new computer. This how-to will explain how to reinstall the Windows XP operating system (with similar rules applying to its predecessors) without the need of the Windows XP CD.
1. Understand that after a while your computer will start to slow down, freeze and sometimes not even shut down correctly. These symptoms are perfectly normal for operating systems that require a clean, fresh start. But sometimes manufacturers do not include a copy of the operating system on a disk to save you money when purchasing your computer and ultimately save them money too.
2. Access the copy of the operating system on the hard drive. If manufacturers do not supply a Windows XP OS (Operating System) CD with the purchase of your new computer, they have most definitely stored a copy in your hard drive for later use. You can easily access this copy of the CD on your hard drive to completely reinstall or format partitions on your computer.
3. Make sure you have your Windows product key/serial number. This could be located on the computer itself, or in the original packaging it was supplied with. If you do not have one, contact your manufacturer immediately for more support regarding the issue.
4. Access path C:\WINDOWS in My Computer. Find a folder named "i386". If you can’t find this folder please see the Tips & Warning section. [Remember you can find this folder only if manufacturer has stored a copy of OS on your Computer]Open it.
This is the a part where a lot of people get confused. They realize that a copy of there Windows OS CD is here, but they look for the incorrect files. Most people will try to find a file named "Setup", "Install", or "Windows". The file you are looking for is called "winnt32.exe".
5. Open this application and proceed with the instructions given. It will lead you through 5 simple phases that will wipe out your computer and reinstall the operating system.
6. Get your product key ready to enter it. Make sure you agree with the terms that should be provided when using the winnt32.exe application.
7. If you are using any operating system below Windows 2000 or Me, try looking for the winnt.exe application as the winnt32.exe application may not be availible for your version of the Windows OS in the I386 folder.
Winnt.exe uses a command driven interface, and therefore requires simple commands to use to reinstall windows or format partitions.
You can find these simple commands at Microsoft’s website :
[http://www.microsoft.com/technet/prodtechnol
/windows2000serv/reskit/deploy/dghm_stp_codt.mspx?mfr=true]
Tips & Warnings
• Make sure you close any unnecessary software and applications that run in the system tray like Windows Live Messenger, Yahoo! Instant messenger and others, before using winnt32. This should speed up the whole process.
• Make sure you have backed up all of your files before you clean out your computer.
• Make sure you have all the required softwares on CD to reinstall the drivers that will be wiped out.
• For some of the lower versions (operating systems) of the Windows franchise, you may wish to use the winnt.exe application instead which will use the Command Prompt application and require certain commands to operate. The Winnt32.exe application may not be available for those who use any OS below Windows 2000/Me.
• If you are having trouble finding the folder, download WinACCESS, it searches your Windows folder for the Windows CD and executes it straight from your hardrive. This small software can also proove useful if the manafacturers installed it to a different location (which in many cases is unlikely).
Warnings
• All drivers will be wiped clean. That includes graphic cards, audio drivers, wireless drivers, etc. Make sure your manufacturers has supplied you with the correct softwares to reinstall the drivers that will be lost on reinstallation of the OS.
• Do not forget to back up all of your data with a system restore tool, or else everything will be lost. This means all software and programs currently installed on the computer.
• Remember Microsoft will not take any responsibility for anything that may go wrong and cause damage to your computer system.
• If the I386 folder or Winnt32.exe/Winnt.exe application does not exist, or you cannot find it, use the Search feature to help you (Start>Search). If it does not wield any results, a copy of the CD may not have been stored on your hard drive. Contact your manufacturer for more support.
Using Disk Defrag on Windows XP
Accessing Disk Defragmenter
• Start | All Programs | Accessories | System Tools | Disk Defragmenter
• Start | Run | and type dfrg.msc in the Open line.
Click OK
• Start | Administrative Tools | Computer Management. Expand Storage and select Disk Defragmenter
The first two methods take you to a standalone window containing Disk Defragmenter. The last method opens Microsoft Management Console and displays Disk Defragmenter as one of the snap-in modules. In all cases, a window similar to the one below will be displayed.
When Disk Defragmenter first opens you'll see a list of the hard drives displayed at the top of the screen. The Estimated Disk Usage Before Defragmentation and Estimated Disk Usage After Defragmentation will be blank until a drive is selected and the Analyze button is clicked. In the screen shot above, I've already analyzed the drives as evidenced by the Session Status showing as Analyzed and the Estimated Disk Usage Before Defragmentation area containing a graphical representation of the drive fragmentation.
After the Analyze button has been clicked and the process completes the window shown above (Fig. 02) opens with a brief recommendation of what action Disk Defragmenter thinks should be taken regarding the drive. It's important to note that this is just a recommendation based on the percentage of fragmented files to total files and doesn't prevent the drive from being defragmented if you feel it needs to be done and might improve system performance. If you want to go ahead and defragment without more information, click the Defragment button. If you're in agreement with their recommendation and don't want to defragment, click the Close button. Click the View Report button to view a more detailed drive analysis.
An Analysis Report contains quite a bit of additional information about the selected drive. The report shown above (Fig. 03) details the File Fragmentation status of drive New Volume (D:). The top pane provides Volume information, and as you can see there are 3,851 fragmented files. This may not seem like many fragmented files, but consider that this is only a 29GB drive, which is very small by today's standards, and that 97% of the total drive space is currently unused. Look at the Average Fragments Per File number of 1.04 and this tells you that approximately 4% of the files on the drive are in two or more pieces. My experience has been that when this number reaches 1.05 the message in the quick analysis window (Fig. 02) will recommend defragmenting the drive. The bottom pane, Most Fragmented Files, lists the files in descending order that are the most fragmented.
Click on Defragment button to Defrag the drive.
You can see the status of Defragmentation in the status bar.
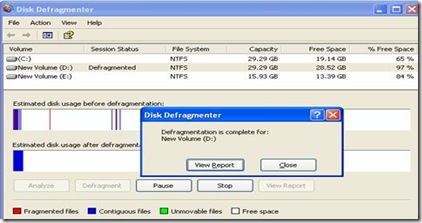
Disk defragmentation is now complete, click on View Report button to view the Defragmentation Report.
In spite of the recommendation not to defragment this particular disk, I went ahead and clicked the Defragment button. The results of that choice are shown above (Fig. 04) in the Estimated Disk Usage After Defragmentation section. The graphical representation clearly shows that not only have the red lines depicting fragmented files been eliminated, many of the contiguous files indicated by the blue have been repositioned toward the beginning of the drive, reducing the amount of searching the drive heads have to do to locate a file. The drive in this example is not a system drive, nor does it have a paging file which would be indicated by the lime green Unmovable Files color.
After the defragmentation process completes, clicking the View Report button will bring up the Defragmentation Report (Fig. 05). It takes the exact same form as the Analysis Report (Fig. 03) but shows the post defragmentation results. The Total Files and Average File Size remain identical, but notice that Total Fragmented Files and Total Excess Fragments have been reduced to zero (0) and the Average Fragments Per File is now 1.00, indicating most or all of the files are contiguous. In addition, there are no files listed that did not defragment.
June 22, 2009
ATM Tips

ATM?
There is no such defined formula that can assurance you about the security of the ATM selection. Therefore, the ATM user needs to exercise some carefulness when selecting an ATM.
There are some steps to fellow:
• Always go for banking in daylight hours and specially avoid to visiting ATM at weekend night.
• lways choose ATM location which you are most familiar, most nearest point from your home or heavily traveled areas.
• First observe the surroundings of ATM before make any transaction, if there are any person looking you then tries to avoid using ATM this time.
• The best practice is that always go for ATM with any family member or with your best friend.
• Avoid using if you find any other machine or code reader attached with the ATM machine.
• Always select the ATM that is monitored by bank security or with security camera.
ATM Tips
Using an ATM
• Be careful when any strangers offer to help you at an ATM, even if your card is block by machine or you are experiencing difficulty with the transaction.
• Check your surrounding any other person in the queue keep an acceptable distance from you.
• Stand very close to the ATM and shield the keypad with your hand when keying in your PIN code otherwise any other person can guess your number.
• Press the Cancel key on keyboard when you find the ATM is not working properly and withdraw your card. Avoid force your card into the card slot.
• Always keep your printed transaction record so that you can compare your ATM receipts to your monthly statement.
• If your card jammed in ATM, report this immediately to the bank.
ATM Tips
Manner to use your ATM
• Try to memorize your PIN code and avoid writing it down on public access book, doing so on secret book.
• Never tell your PIN to any third person, whether to family member, office staff.
• Avoid using easily guessable numbers for your PIN code for example your date of birth, your phone number and others.
• Change your PIN code on weekly basis.
• Weekly check your account balance and bank statements if you find any problem, contact to your bank immediately.
June 20, 2009
Smart Card
A smart card resembles a credit card in size and shape, but inside it is completely different. First of all, it has an inside -- a normal credit card is a simple piece of plastic. The inside of a smart card usually contains an embedded microprocessor. The microprocessor is under a gold contact pad on one side of the card. Think of the microprocessor as replacing the usual magnetic stripe on a credit card or debit card.
Smart cards are much more popular in Europe than in the United States. In Europe, the health insurance and banking industries use smart cards extensively. Every German citizen has a smart card for health insurance. Even though smart cards have been around in their modern form for at least a decade, they are just starting to take off in the United States.
Magnetic stripe technology remains in wide use in the United States. However, the data on the stripe can easily be read, written, deleted or changed with off-the-shelf equipment. Therefore, the stripe is really not the best place to store sensitive information. To protect the consumer, businesses in the U.S. have invested in extensive online mainframe-based computer networks for verification and processing. In Europe, such an infrastructure did not develop -- instead, the card carries the intelligence.
The microprocessor on the smart card is there for security. The host computer and card reader actually "talk" to the microprocessor. The microprocessor enforces access to the data on the card. If the host computer read and wrote the smart card's random access memory (RAM), it would be no different than a diskette.
Smarts cards may have up to 8 kilobytes of RAM, 346 kilobytes of ROM, 256 kilobytes of programmable ROM, and a 16-bit microprocessor. The smart card uses a serial interface and receives its power from external sources like a card reader. The processor uses a limited instruction set for applications such as cryptography.
The most common smart card applications are:
• Credit cards
• Electronic cash
• Computer security systems
• Wireless communication
• Loyalty systems (like frequent flyer points)
• Banking
• Government identification
Smart cards can be used with a smart-card reader attachment to a personal computer to authenticate a user. Web browsers also can use smart card technology to supplement Secure Sockets Layer (SSL) for improved security of Internet transactions. Visa's Smart Card FAQ shows how online purchases work using a smart card and a PC equipped with a smart-card reader. Smart-card readers can also be found in mobile phones and vending machines.